Search Results
151 items found for ""
- Can 2 or More Monitors Increase Staff Productivity?
Looking for ways to help your team accomplish more? Consider equipping their workspaces with additional monitors. Skeptics are likely shaking their heads at this, wondering, “Will that really improve productivity, or only give my employees an extra incentive to stream videos or play games? Aren’t more screens just a recipe for distraction?” Believe it or not, business leaders recommend providing your employees with two or more monitors. Here are just a few reasons why multiple monitors should be on your radar screen: Digital Decluttering It’s well-known that a messy workspace typically leads to chaos and confusion. Working at a crowded or disorganized desk requires you to navigate piles of paperwork or jumbles of office supplies to get things done. A cluttered desktop computer has the same effect. An abundance of icons and open tabs creates headaches for your team, while a second monitor keeps apps and programs organized. Higher Productivity Industry leaders report that productivity increases with two or more monitors. Users can navigate multiple applications efficiently, view more information simultaneously, and customize each monitor’s layout– with different landscapes and resolutions– to optimize ease-of-use. Most modern computers are designed with multiple-monitor systems in mind. That means your employees can enjoy the benefits of added data availability without having to learn a new software program or spend valuable time configuring a new system. Those advantages alone are enough to boost productivity and streamline workflows. It’s also worth mentioning that Windows automatically “remembers” which monitor you last used to open a program, defaulting to that screen when you need to access the program again. When you’re multitasking or working on a big project, you can keep application accessibility consistent to maximize efficiency. Versatility Multiple screens prove invaluable in a variety of occupations– from graphic design to market analysis and stock-trading. You can easily make use of multiple applications and copy, paste, and edit data and images when you have access to more than one monitor. If your marketing team uses social media to promote your brand, they can reserve one screen for Twitter and Instagram and keep other documents open on another. Likewise, if you must frequently respond to email, you can glance up from your work occasionally to check the other monitor for new inbox arrivals, rather than having to toggle back and forth within one screen, which can make digital correspondence more of a distraction than it has to be. Workstations with extra monitors are also helpful for people who use laptops and need to frequent multiple workspaces throughout the day. Some companies provide “docking stations” where employees can connect a laptop to multimedia equipment– such as a monitor, speakers, and wireless keyboards– to access data, utilize a particular application, or perform other tasks. This is more cost-effective and efficient than providing each employee with a desktop and a laptop. Data-Sharing and Referencing When meeting with colleagues, you can effectively keep them “in the know” by enabling them to view the same information simultaneously. Whether you’re presenting information to a small group or a larger crowd, multiple monitors can be adjusted to display information from different angles, making it highly-visible to everyone. Similarly, if you are communicating with clients and vendors, you can track inventory or an order’s status without putting people on hold while you look up the information. When preparing reports, you can have a PDF or HTML file open on one screen for reference while you create a Word document or Excel spreadsheet on another. If you have more than two monitors, you can keep other pertinent information within easy reach, too, allowing you to transition more smoothly from one task to the next. Collaboration When teleconferencing via Skype or a similar app, you can make your data visible to colleagues while still communicating almost as though you were face-to-face. Displaying data on one screen while video-chatting on another allows you to keep the interaction personal without compromising data accessibility. The idea of providing multiple monitors for your staff may seem counterintuitive at first, but the advantages outweigh potential drawbacks. When you make dual-monitor systems a staple of your workplace, using them will become second-nature, especially when you see how they make it possible to move so effortlessly from one application to another. This low-maintenance solution gives your team the opportunity to get more accomplished in less time and paves the way for better communication and collaboration. All these benefits can go a long way toward improving morale and serving as a catalyst for enhanced creativity and innovation.
- 5 Indicators that an Email Might be a Phishing Attempt
As Phishing continues to be a large concern for businesses both large and small. We have compiled a list of 5 indicators that an email might be attempting to phish personal / business information out of you and your employees. Learn more about what phishing is and why it is a threat here. Request of login credentials – Any legitimate company will not ask for you login credentials via email. If you get any emails that ask for you to reply back with your login credentials (or any other personal or business information) it is always best to go the web browser and go directly to the company's website, login there, and see if you have any messages or notifications. Never reply back with any sensitive information even if the request appears legitimate. Link included asking for personal information – On a similar note, if you are sent an email that includes a link that asks you to enter any sensitive information (login credentials, SSN, banking information, etc.) it is best to double check with the source before entering any of the requested information. Criminals can successfully trick targets with links by making the landing pages, when clicked, look incredibly realistic and hard to distinguish that you are actually at a fake site attempting to collect information. Again, it is best practice to go directly to the website you are familiar with by entering the address in your web browser and entering any personal information from there, rather than clicking any links that come via email. If you are ever suspicious, reach out to a customer service representative at the company before clicking on a link. False sense of Urgency created – One way the cyber criminals target victims is by creating a false sense of urgency to trick you into doing something without fully thinking it through. If you receive any emails that are asking you to do a task or give personal information and are being asked to do it urgently, there is a good chance you are being targeted for phishing of your confidential information. It is always best practice to check with the source directly, whether it be a coworker, someone you work with elsewhere, or a company you are familiar with, before acting on any request that comes in via email, especially when a short time-frame is specified. Spelling/Grammar Mistakes – An easy way to weed out phishing emails is by paying attention to grammar and/or spelling mistakes. While we all occasionally fall victim to making an error when sending an email, phishing emails are often written by a criminal who is not fluent in English and will make errors in his/her spelling/grammar. If an email is pretending to be from a legitimate company or contact and has spelling/grammar issues that stand out it is very likely from a cyber criminal attempted to phish for confidential information. Includes an attachment or download that was unexpected – If an email includes any sort of attachment or links you to a location to download something it is always best practice to double check before clicking or downloading. Cyber criminals will often infect devices by getting victims to download items that may appear legit but can sit in the background and infect machines and collect information over time. You can go directly to the trusted website via your web browser and download attachments there if possible as well. What if I may have clicked on a phishing link? If you do happen to click on a link that seems suspicious contact your IT staff at 1.800.358.7447 right away. Once you have clicked a phishing link, your computer can be vulnerable to ongoing phishing methods and your personal information could be un-secured. Have questions about phishing or other cybersecurity topics? Your security experts at Mapletronics are available to help. Contact us here or call us at 1.800.358.7447.
- Email Protection
To login into the Email Protection Control Console and manage your protection browse to: emailprotection.mapletronics.com and enter your username and password. FAQs How do I change what Email Protection blocks? From the Email Protection Control Console click on the "Quarantined" button. If an email has been caught by the spam filter, you can select that message and click "Allow Sender". You can do the same thing if you wish to block certain email addresses or domains by selecting the "Deny Sender" button. For more info on this please view the Email Protection User Guide (video). How do I use Email protection to view and send emails if my email server is offline? From the Email Protection Control Console click on the "Continuity" under "Messages", from here you will be able to continue using your email from the web interface until your email server is back online. Why does a Web browser open when I try to do anything on my Spam Quarantine Report? The Spam Quarantine Report provides an easy-to-use connection into the appropriate feature in the Control Console. The Control Console is a Web-based graphical user interface and is the primary interface to Email Protection. When a user clicks a link in the Spam Quarantine Report, it causes the default Web browser to open, automatically logs the user into the Control Console, and performs the action designated in the clicked link. There are emails in my quarantine that I want to always receive. I clicked the “Always Allow” button, but the emails still get caught – What am I doing wrong? The user-level Allow list does not disable virus, content, or attachment filtering; it only disables the spam filtering. If the email violated any of the enabled policies, it would be filtered even if its sender address was added to the user-level Allow list. In addition, companies often send items in a format that looks like spam that a user may have opted to receive, such as electronic newsletters or emails, causing the email to be quarantined. When a user clicks the Always Allow link in the Spam Quarantine Report or the Spam Message Quarantine window, the sending email address is added to the user-level Allow list. However, for various reasons, emails of this nature may not always come from the same address every day. Because senders often rotate the address of these types of emails, the same item could be delivered the very next day and still be blocked because the sender address does not match the previous entry in the Allow list. To help prevent this situation, you can use wildcards to designate an entire domain or part of an email address (if there is a common pattern) to be added in the Allow list, thus accepting all mail from the domain or email addresses that matched the designated pattern. I’m receiving spam email from my own email address and I know I didn’t send it. What’s happening and how do I stop it? A spammer has “spoofed” your email address. Spoofing means that the “From:” address in emails has been falsified to be an address other than the real source of the emails. The intent is to trick the recipient into opening the email because it appears to be from a trusted source. In your case, they made the mistake of using your own email address as the spoofed address and you realized that you had not sent the email. Spoofing is illegal according to the CAN-SPAM Act of 2003; however, it is still a common tactic used by spammers. You can do any of the following in Email Protection to block these types of emails. Confirm that your own email address is not in your Allow list. It is possible that the spoofed email would be caught by normal spam filtering; however, if your email address is in an Allow list, spam filtering will be disabled. If necessary, remove your email address from any Allow lists to make sure spam filtering is performed.Add your own email address to your user-level Deny list This policy will automatically deny any emails received from your email address. It will apply to all emails received from the Internet into Email Protection that are filtered and then sent to you. It will affect only emails sent to your address. Note: Using a Deny list as a filtering tactic in this situation will succeed only if your corporate email is not sent into the Internet cloud before delivery to other addresses in your Domain name. The assumption is that your corporate email is delivered within your internal network without filtering by Email Protection. If your organization does deliver your corporate email using a delivery method that includes sending it into the Internet, it is possible that valid corporate emails will be filtered if you make the above policy changes.
- 31 Cybersecurity Terms Everyone Should Know
A key part in protecting yourself and your business from being a part of a security breach is to stay educated on security. As cybersecurity issues regularly become more complicated and are changing at a rapid speed it is important to know the terms and language that is being used to describe these cybersecurity events. We have compiled a list of 31 cybersecurity terms that you need to know to begin to understand the cybersecurity landscape and keep yourself, your employees, and your business protected. Adware – You see this pop up when you get unwanted advertisements appearing on your screen when you visit certain sites. Adware is highly problematic because it can not only disguise itself as a legitimate site and trick you into clicking buttons that actually trigger the download of software that can track you to collect data on your activities, but it can also add harmful software to your device. Application Security - A process for enhancing the security posture of software. The process typically involves: threat modeling, design reviews, finding security bugs through tools/testing (IAST, RASP, SAST, DAST, manual, etc), and then fixing the security bugs in the software development lifecycle (SDL). Application security is being adapted in to more streamlined ‘DevSecOps’ processes in today’s development world. Authentication – This refers to the sequence of steps by which the identity of a user or device is verified. Single passwords are the simplest form of authentication. Current best practices are for multi-factor authentication, where multiple different checks are used to verify identity since hackers are less likely to be able to provide various forms of verification. Blacklist – Any collection of users, devices, or other entities that are not permitted access privileges. Bot – An individual device that has been fed programming to act maliciously under the remote control of another administrator. Bug – A functional glitch or imperfection present in a device or piece of code. Certificate – This is virtual confirmation of the identity of a specific entity. This is usually issued by a Certificate Authority (CA) and is something that can be verified. When you visit a secure site, for example, your computer checks the site’s security certificates and in this way determines that the site is secure. Cloud - Emerging technology that allows us to access our files and/or services through the internet from anywhere in the world. Technically speaking, it’s a collection of computers with large storage capabilities that remotely serve requests Cyber exposure - An emerging discipline used to accurately understand and reduce cyber risk. This approach is key to helping companies safeguard valuable assets and become more cyber secure by providing holistic visibility into the various digital compute platforms and assets that make up the modern attack surface. The Cyber Exposure process takes the whole life cycle into account, allowing companies to determine where they are exposed, where they should prioritize based on risk and how they are reducing exposure over time Data breach – Any event where information is shared with an untrustworthy party or opened up to an unsecured environment. Data mining – The analysis of large data sets to identify previously unknown patterns or relationships. Often used towards positive ends, such as in medicine to discover health trends in populations or in academia to characterize social patterns, data mining can also be employed for malicious purposes by hackers. Distributed Denial of Service (DDOS) – This is a form of attack that targets a specific server or network of servers, causing a massive, sudden surge in traffic with the intent of shutting down the servers. One of the most common ways for this to take place is for a hacker to use malware to gain access to several machines connected on the same network; these can then be controlled by the hacker or directs them to flood the network servers. Encryption – This is a process of data conversion that transforms it using a secret code into a sequence that requires deciphering to be able to use; only authorized entities have the means to decode this sequence and access the data contained within. Endpoint - Endpoint refers to any device that connects to a network and can serve as an entry point for security threats. Devices such as smartphones, tablets and laptops are all endpoints that must be secured to block unauthorized access to company networks. Endpoint security also can prevent the internal theft of sensitive data. Firewall – This can be constructed using software and/or hardware, but at its core, it sets a specific set of access permissions in place that control who can access a particular network. Secure firewalls offer several layers of protection from hackers and their malware. Honeypot – This is a fake vulnerability that masquerades as a weakened part of your system or network, in an effort to bait a potential hijacker or other threat. It can be used as part of a security plan as a way to monitor whether the system or network is currently a moving target for any threats. IP Address - A unique series of numbers that identifies a device connected to the Internet or a local network. Allows systems to be recognized by other systems via Internet Protocol. IoT Security - Internet of Things (IoT) security includes both the physical security of internet-connected devices and the network security to which each IoT ‘thing’ connects. Keylogging – This is generally a malicious practice where keyboard input is secretly monitored as a way to keep tabs on a user’s activity. Aside from the violation of personal privacy inherent to this, this is particularly dangerous as it gives hackers access to input personal details such as credit card information and passwords. Malware – This is a broad term that refers to any software that intrudes upon a computer system’s process in an unauthorized manner. MSSP - MSSP stands for ‘managed security service providers.’ They provide outsourced monitoring and management of security devices and systems. MSSP can be outsourced or managed in-house. Services include firewall management, vulnerability scanning, and anti-viral protection. Phishing – This refers to the practice of using false communications to deceive people in a way that elicits their sharing of personal information and sensitive details. One typical example of phishing is when scammers send emails pretending to be the Internal Revenue Service or a bank, and scaring recipients into believing they are in trouble and need to resolve a conflict. This resolution always requires the user to share details so that they may be identified. Ransomware – This is a form of malware that cannot be removed until payment of a ransom is received by the malicious instigator. The most common avenues for spreading ransomware include infected websites as well as phishing. Spear Phishing - A technique used by attackers to obtain sensitive information. Traditionally executed using highly targeted email messages designed to trick people into divulging personal or confidential data. Spoofing – This refers to any method by which a user is conned. Successful spoofing is what leads users into sharing their details with the malicious party. For example, the impersonation involved with many phishing scams is an example of spoofing. Spyware – This is malware that is secretly placed onto a system and monitors the user’s activities. Threat – This is an imminent risk to exploit known or unknown opportunities for malicious individuals or organizations to infiltrate a system or network. Virus – A piece of programming code that can secretly enter a computer, replicate, and then be transmitted to other computers. Vulnerability – This is any potential opportunity for malicious individuals or organizations to infiltrate a system or network. Threats exploit vulnerabilities; and so, it might be a flaw in design or a gap in security protocols. Whitelist – The opposite of a blacklist, this is a list of exclusions to a particular security rule, generated because the members of the list are known to be trustworthy. Zero day exploits - A cyberattack on a software or hardware vulnerability before it can be detected and fixed. Attackers exploit the security flaw by releasing malware that can take control of your computer, steal your data, corrupt files, access your contacts, and send spam messages from your account. At Mapletronics, we value our position as your security experts. We hope that this list can be a guide to understanding confusing cybersecurity terminology. Our expert team is always here to help if you need help deciphering a term or understanding what is happening in the world of cybersecurity. We view it as our job to stay one step ahead of malicious acts and security breaches and we hope to help you prevent hackers from successfully infiltrating their way into your business.
- HIPAA Security Rule Resources
The Security Rule (and then some) Are you responsible in whole or in part for taking care of HIPAA Security Rule compliance in your organization? Have you actually read the Security Rule? If not, it's the perfect place to start. You'll find all of these rules in this Combined Regulation Text from HHS: Transactions and Code Set StandardsIdentifier StandardsPrivacy RuleSecurity Rule (Located at 45 CFR Part 160 and Subparts A and C of Part 164)Enforcement RuleBreach Notification Rule Combined Regulation Text (updated, March 2013) - Download HHS's HIPAA Security Series The HIPAA Security Series provides guidance and insight into the Security Rule. It addresses every Standard (22 of them) and Implementation Specification (42 of them) by explaining the essence of each requirement, the thought process behind them, and some possible ways to address them. These papers are relatively easy to read and do a good job of putting the government-speak into everyday language. Security Series #1 - Security 101 - Download Security Series #2 - Administrative Safeguards - Download Security Series #3 - Physical Safeguards - Download Security Series #4 - Technical Safeguards - Download Security Series #5 - Organizational, Policies & Procedures, and Documentation Standards - Download Security Series #6 - Basics of Risk Analysis and Risk Management -- Download Security Series #7 - Implementation for the Small Provider - Download A1 - Guidance on Risk Analysis Requirements under the HIPAA Security Rule - Download A2 - Guidance on Remote Use of ePHI - Download NIST Documents NIST is the National Institute of Standards and Technology. Their Computer Security Division has published several very helpful papers to guide readers through some of the more difficult concepts you'll run into when complying with the Security Rule. These are more in depth than the Security Series (above) and they drill into several of the main elements of compliance. 800-66 - An Introductory Resource Guide for Implementing the HIPAA Security Rule - Download 800-30 - Guide for Conducting Risk Assessments - Download 800-118 - Guide to Enterprise Password Management - Download All NIST 800 Documents Watch Our HIPAA Webinar Series Click the playlist button in the upper left corner to view all HIPAA webinars.
- What will Windows 7 End of Life Mean for My Business?
Windows 7 "End of Life" date is quickly approaching. The official end of life date is January 14, 2020. "End of Life" means Microsoft will discontinue all support, including paid support, and all updated including security patches and updates. What does "End of Life" mean? "End of Life" is that date after which an application is no longer supported by the company that makes it. You can still use Windows 7 after it's "end of life" date but you are doing it essentially at your own risk. New viruses and malware are developed at rapid speeds in today's cybersecurity climate and without security updates to fight them off, you are leaving your systems and data in a vulnerable state. Upgrading from Windows 7 Upgrading from Windows 7 to the new Windows 10 is the recommended course of action. Upgrading to Windows 10 will give you access to apps that can be used across multiple devices, including PCs, tablets, and smartphones. Windows 10 is faster than Windows 7 and includes many other benefits as well. For more information on Windows 7 "End of Life" and updating to Windows 10 contact us today.
- Increase Productivity with the Ultimate List of Windows 10 Shortcuts
Who doesn't desire more productivity in their workday? A simple way to maximize your time when using a computer is to have a go-to list of shortcuts that you can learn and memorize to cut down on the time it takes to do regular every day tasks. Below you'll find a list of 50 Windows 10 shortcuts that can help you cut down on the time it takes to complete day to day tasks. Do you have a favorite shortcut that you don't see on our ultimate list? Let us know and we may add it to our list. Windows key | Open or close Start Menu. Windows key + A | Open Action center. Windows key + C | Open Cortana in listening mode. Windows key + D | Display and hide the desktop. Windows key + E | Open File Explorer. Windows key + G | Open Game bar when a game is open. Windows key + H | Open the Share charm. Windows key + I | Open Settings. Windows key + K | Open the Connect quick action. Windows key + L | Lock your PC or switch accounts. Windows key + M | Minimize all windows. Windows key + R | Open Run dialog box. Windows key + S | Open Search. Windows key + U | Open Ease of Access Center. Windows key + X | Open Quick Link menu. Windows key + Number | Open the app pinned to the taskbar in the position indicated by the number. Windows key + Left arrow key | Snap app windows left. Windows key + Right arrow key | Snap app windows right. Windows key + Up arrow key | Maximize app windows. Windows key + Down arrow key | Minimize app windows. Windows key + Comma | Temporarily peek at the desktop. Windows key + Ctrl +D | Add a virtual desktop. Windows key + Ctrl + Left or Right arrow | Switch between virtual desktops. Windows key + Ctrl + F4 | Close current virtual desktop. Windows key + Enter | Open Narrator. Windows key + Home | Minimize all but the active desktop window (restores all windows on second stroke). Windows key + PrtScn | Capture a screenshot and save in Screenshots folder. Windows key + Shift + Up arrow | Stretch the desktop window to the top and bottom of the screen. Windows key + Tab | Open Task view. Windows key + "+" key | Zoom in using the magnifier. Windows key + "-" key | Zoom out using the magnifier. Ctrl + Shift + Esc | Open Task Manager. Alt + Tab | Switch between open apps. Alt + Left arrow key | Go back. Alt + Right arrow key | Go forward. Alt + Page Up | Move up one screen. Alt + Page down | Move down one screen. Ctrl + Alt +Tab | View open apps Ctrl + C | Copy selected items to clipboard. Ctrl + X | Cut selected items. Ctrl + V | Paste content from clipboard. Ctrl + A | Select all content. Ctrl + Z | Undo an action. Ctrl + Y | Redo an action. Ctrl + D | Delete the selected item and move it to the Recycle Bin. Ctrl + Esc | Open the Start Menu. Ctrl + Shift | Switch the keyboard layout. Ctrl + Shift + Esc | Open Task Manager. Ctrl + F4 | Close the active window.
- Increase your Productivity with these 5 Office 365 Tips
Looking to increase your productivity (let’s be honest who isn’t!)? Here are 5 tips and tricks for Office 365. Do you have a favorite tip that's not featured here? We'd love to hear from you. Join the conversation and comment with your favorite below. 1. Collaborate with Teammates in Real Time by Editing Documents Together New to Office 365? You might not realize that it’s now an online service. You can now edit a document from Word, Powerpoint, or Excel and share the link giving others access to see the changes you make in real time and make changes themselves as well. Long gone are the days of circulating versions of documents, now you can all log in at once and work on the document together. 2. Share Files by Link instead of Attachment With access to the business edition of Office 365 you can share a fire instead of attaching it. Upload your file to Office 365's cloud storage, fire up the cloud version of Outlook and instead of attaching a file, link to the file on your cloud. Outlook will automatically grant edit permission to the people you are emailing. (You can change their permissions as well). 3. Turn Notes Into Calendar Items You can use OneNote inside of Microsoft Outlook to quickly convert your to do or notes into a calendar item. Write up a to-do list in OneNote, and easily convert it into a bunch of tasks with deadlines and reminders on your calendar. More info here. 4. Teach Your Inbox to De-Clutter Itself The clutter feature in Outlook takes any and all rules you have set up for your inbox and uses them to understand your email preferences. It will take your preferences and use them to automatically move less important messages in the "clutter" folder for you to read or delete later. Learn how to set up your clutter folder here. 5. Add an Electronic Signature to an Email Looking to add your electronic signatures to your email? Docusign now offers a free app available for Outlook that lets you do just that. Add the app and learn more here. Do you have a favorite tip that's not featured here? We'd love to hear from you. Join the conversation and comment with your favorite below.
- 10 Tips for Improving and Customizing your Windows 10 Experience
Whether you upgraded to Windows 10 right after it became available or you are just now making the switch there are some tips & tricks that you may not be aware of that can improve and customize your experience. We’ve round 10 of our favorite tips & tricks for Windows 10 below. 1. Customize your start menu Unless you’ve been living under a rock you’ve probably come across a Windows Start Menu a time or two in your life. The stylized window icon in the corner of your screen is your key to accessing Windows 10’s version of this iconic menu. You can change the appearance of your start menu by right-clicking on an icon in the menu or by touching and holding the icon for a few seconds if you’re using a touch screen. You can also right click the start icon which will show a quick and clean menu. This puts more options at your fingertips including the Task Manager, Control Panel, Device Manager, and even the Command Prompt. 2. Disk cleanup to add some space As computers have gotten more sophisticated and had larger RAM, the usefulness of the Disc Cleanup tool has decreased. However, Disc Cleanup still holds value in quickly deleting files and ensuring your recycle bin is cleared out. In Windows 10 just type “disk cleanup” into your taskbar where it says, “Type here to search” >> click on the Disk Cleanup app >> Put a check mark next to each folder you want to be deleted and you’ve cleared up some space. 3. Quickly open the Taskbar Using new intuitive shortcuts in Windows 10 you can have quick access to some of your most used apps. The taskbar at the bottom of your screen has program icons lined up, most likely some of these include your web browser and the windows files explorer, as well as others. You can quickly open these programs by hitting the Windows key and the number that corresponds to the location of the icon on the bar. For example: if you have Chrome in the first position on the left in your task bar and press the Windows key and the number 1, Chrome will open up. 4. Stream Video You can steam videos on your TV using Windows 10. Using compatible devices such as Roku and Xbox One S. Just type “media streaming” in the Windows 10 taskbar >> Select media streaming options and follow the instructions 5. Find programs that are slowing you down What’s more frustrating than trying to work on your computer and your computer moving slow as molasses? Not much! When you run in to this issue you can use the task manager to find out what’s slowing it down. Open the task manager and check out the “Processes” tab. It will show you which apps and background processes are running and how much of your CPU, memory, and disk and network resources they are taking up. 6. Use the updated Task Manager Not only can the task manager be used for the tried and true purpose to force-quit unresponsive programs, in Windows 10 it got an upgrade making it a much more robust tool. You can quickly access it by hitting control-alt-delete 7. Quickly find your apps Opening the regular Start Menu lets you see a list of your apps running down the side. The most-used apps are on the top and the rest are laid on in alphabetical order. You can scroll through all of the apps but if you have quite a few this can be cumbersome. By clicking on the main letters (like “A”) when browsing you an alphabet menu appears that lets you click on the first letter of the app you want and taken directly to that part of the start menu. 8. Use the Task Scheduling tool Here’s a tool that does just what its name implies. You can find it by typing “Task Scheduler” in the taskbar. Use the taskbar to help schedule task on your computer, like turning it off at a specific time each day. 9. Print files as PDF PDF is a format that is compatible across most operating systems and software programs. You can quickly convert a file to a PDF in Windows 10 by printing as you normally would and selecting “Microsoft Print to PDF” when prompted to select what printer you’d like to use. 10. Record your screen Here is a quick way to record your screen. Click on the Windows key on your keyboard and the letter G at the same time. Follow the prompts and record.
- What is Microsoft Teams and Why Do We Love It?
Unless you’ve been living under a rock, you’ve probably either heard about or are already using a collaborative program to chat with coworkers. Teams is Microsoft’s take at a “chat based workspace” that allows for real-time collaboration and allows people to come together to have casual conversations and create work plans. Why move to a group chat environment? It is significantly easier to use than traditional email. You can easily integrate other apps and productivity tools to bring together everything your team needs to work together efficiently. 3 Reasons Why We love Teams Boosts collaboration and productivity Collaboration and productivity is at the top of the list for goals for most businesses. Microsoft Team’s is a well-designed solution that is built to boost collaboration and productivity in businesses using Office 365. The idea behind teams is to make a digital translation of an open office space. Whether users are all together in a physical office or scattered around the world Teams allows for chat communications, file integration, and other applications all structed in a cohesive way. Integrates seamlessly with Office 365 Many of you are probably already using Office 365 making Microsoft Teams and easy add on feature that only extends your use of products you’re already using every day. When teams are created, a fully functional group is also created. This creates an associated SharePoint site, mailbox, and OneNote notebook. Teams is also integrated with Exchange so emails and calls can be made from within team itself. Since Microsoft has announced that Skype for Businss will be discontinued, teams is the new place to exchange video and voice conferencing and calls. The files tab in every team uses SharePoint for storage, and more tabs can be added to include collaborative spaces like Excel notebooks, Word documents, calendars and more. It’s Secure With Microsoft Office 365 as the foundation of Teams, you can rest assured knowing that security is a key feature. Teams is Tier C compliant including standards like SOC 1 and 2, ISO27001, HIPAA, and EU Model Clauses. Microsoft Teams states that they “enforce team-wide and organization-wide two-factor authentication, single sign-on thorugh Active Directory, and encryption of data in transit and at rest. Files are stored in SharePoint and are backed by SharePoint encryption. Notes are stored in OneNote and backed by OneNote encryption”. Teams also offeres two-factor authentication and SSO via Active Director or SAML and supports mobile data protection via Intune. As you can see, teams is a robust tool that makes sharing and collaborating with coworkers easier than ever. With the emphasis on transitioning from Skype for Business to Teams, we expect to see the software grow and become even more feature laden as time goes on. If your organization is already using Microsoft Office 365, Teams is a natural and easy transition that will only enhance your experience. If you have any questions about how to begin using teams or want more information on how Teams can positively impact your organization feel free to comment below or contact us for more information.
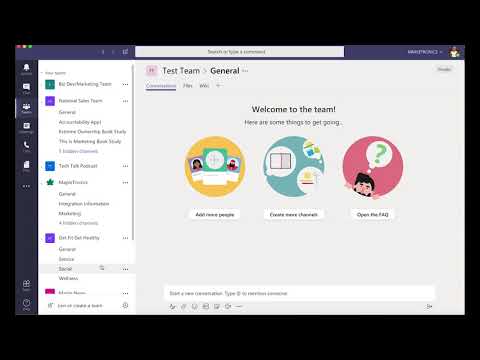
- An Introduction to Microsoft Teams
Are you interested in being more organized and collaborating with your employees/ teammates more effectively? In the fast paced world we live in today, most people would answer yes to that question. Microsoft Teams is a great tool that can help you do just that. If you are already using Microsoft Office 365, you already have access to Teams and can quickly and easily learn how to use it as a tool to make your business run more effectively. What is Microsoft Teams? Microsoft Teams is cloud-based team collaboration software that is part of the Office 365 suite of applications. The core capabilities in Microsoft Teams include business messaging, calling, video meetings and file sharing. The basic functions of Teams Business Messaging - Teams is a tool that can make communicating within your organization easy and effective. When using business messaging within teams you can set up teams/channels and communicate easily within the channel to all members of a team. You can also use the chat features to quickly communicate with individual teammates. Calling within Teams - Calling in Teams is easy! Your teammates phone number will be incorporated within their account, so forget phone lists, just click the teammate you wish to call and place a call. Video Meetings - Teams coordinates with your Outlook calendar to easily schedule meetings with teammates and schedule conference calls/ video conferencing. If you are familiar with Skype for Business, you will find Video Meetings in teams to be quite similar and notice some enhancements within the app. You should also note that teams will soon be replacing Skype for Business Completely. File Sharing - Say so long to searching through email to find shared files. Teams keeps your files organized for you by team/channel/chat so that you never have to look hard to a file that was shared with you. Want to Learn More? This is just the beginning of what Teams can do for your organization. We are excited to be offering a *NEW* Teams training class that will show you the basics and the more advanced functions of Teams. To Learn more and to sign up now visit www.mapletronics.com/training.
- Catch Up on What You Missed at Our Technology Conference
On September 19, 2019 Mapletronics hosted their first Technology Conference at their Goshen, IN office location with live-streaming available for those unable to attend on site. If you were unable to attend the event, we have good news for you. The livestream videos are available for you to watch in full at your convenience. Watch Part 1 Part 1 features the following Key Notes: - Road-Mapping Your Digital Transformation: A documented strategic plan for your organization's digital transformation is critical to its success, but creating such a plan is difficult, and what should that plan look like? Find out how to align your organization's goals, processes and stakeholders; group & prioritize themes for real digital transformation and create a tactical, quarter-by-quarter roadmap you can use to socialize and execute your strategy. - Improving Cybersecurity by Optimizing Human Performance and Judgement: Security breaches can pose great threats to a business. Some breaches render minor effects while others can cause financial liabilities and business disruptions. Learn how human error and process failures account for the majority of breaches and steps you can take to effectively employ an overall strategy to reduce your exposure to breaches. Watch Part 2 Part 2 Includes the Following Key Notes: - Pushing Digital Transformation to the Edge: Digital transformation is typically a top-down strategy that is guided by the CIO. However, while most strategies address large, organization-wide processes, there are hundreds of long-tail business processes that remain in the shadows. Learn how rapid-fire innovations (cloud, mobile and analytics), heavy customization and complexity can dramatically influence the disruption impact when these long-tail business processes get exposed. - Boosting Team Effectiveness in High-Stress Environments: How can a fast-paced organization quickly prioritize and triage issues in today's rapid culture? How does a company ensure timely data is being shared to not only the right people but then also empower those to collaborate and take action in real time? How can a group work on multiple complex projects efficiently all while making sure information is accurate? Learn to leverage your digital workplace platform to create a culture of agility, greater transparency and individual empowerment that leads to a high performing team and increased productivity. Download the slides from the event here. To those who were able to join us for this special event. Thank you for your participation. We hope you found value in your time at our conference.